Intro
When you open a password protected zip archive using Windows Explorer (“Extract All…”); in Windows 8.x/10, the password is automatically cached in the Credentials Manager for the life of the logon session.
Let’s say you discover a host been infected with a malware that coming from a zip file that are password-protected. We can possibly try to extract cached/stored credential from Windows Credential Manager and see if it stores password for password-protected file that we’re looking for.
Steps
To view if the host contains password for file that we needed, run this cmd below (require Admin privileges):
cmdkey /list
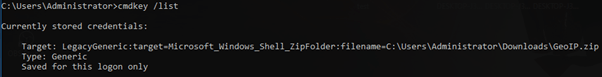
It will show list of stored credential that are available. If your target file is not listed, probably the credential has gone (the host has been rebooted) or the file been extracted using 3rd party apps (WinRAR, 7Zip).
To recover the password, we’ll need to use this Powershell script – https://github.com/zetlen/clortho/blob/master/CredMan.ps1
Download & save the script into target machine. Then, run the script as below:
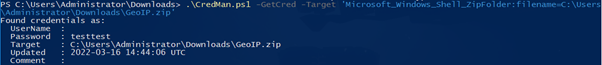
.\CredMan.ps1 -GetCred -Target "target_credential"
e.g.:
.\CredMan.ps1 -GetCred -Target 'Microsoft_Windows_Shell_ZipFolder:filename=C:\Users\Administrator\Downloads\GeoIP.zip'

As you can see, we able to retrieve the “GeoIP.zip” password (pass: testtest).